Secure earlier
Scan throughout your build pipeline, verifying new container images as they’re built and providing continuous zero-day protection after images are published or deployed. Automated scanning and response provide instant feedback to your developers about the presence of threats and vulnerabilities.

Trusted enforcement
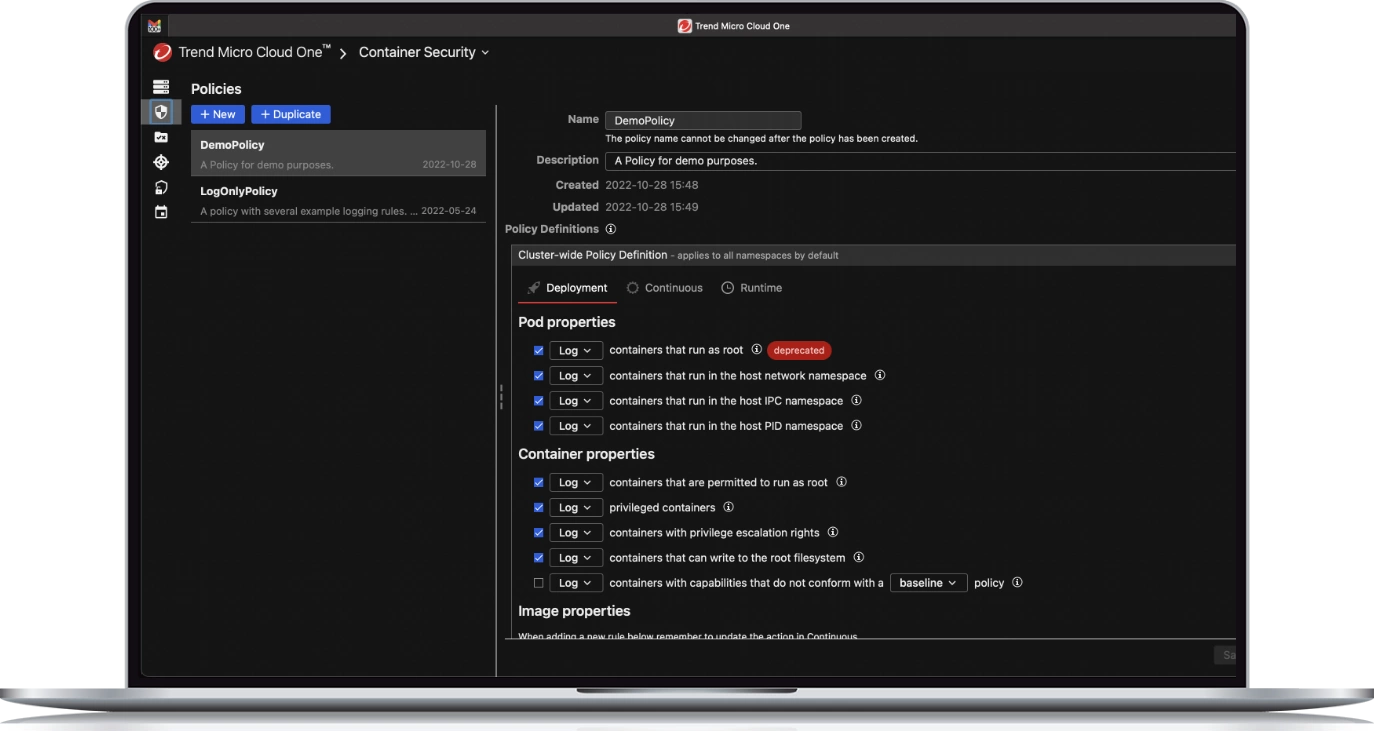
Make centralized container admission control part of your container security approach. Trend Micro provides policy-based management of images, allowing security teams to select and define the rules so that only the most secure Kubernetes administered containers are deployed.

Complete protection
Automate vulnerability detection of malicious traffic and protection of your containerized applications – from commit to runtime. Gain in-depth security coverage built into your CI/CD processes to address container risks for stronger protection.
WHY CONTAINER SECURITY
Early detection, confident deployment
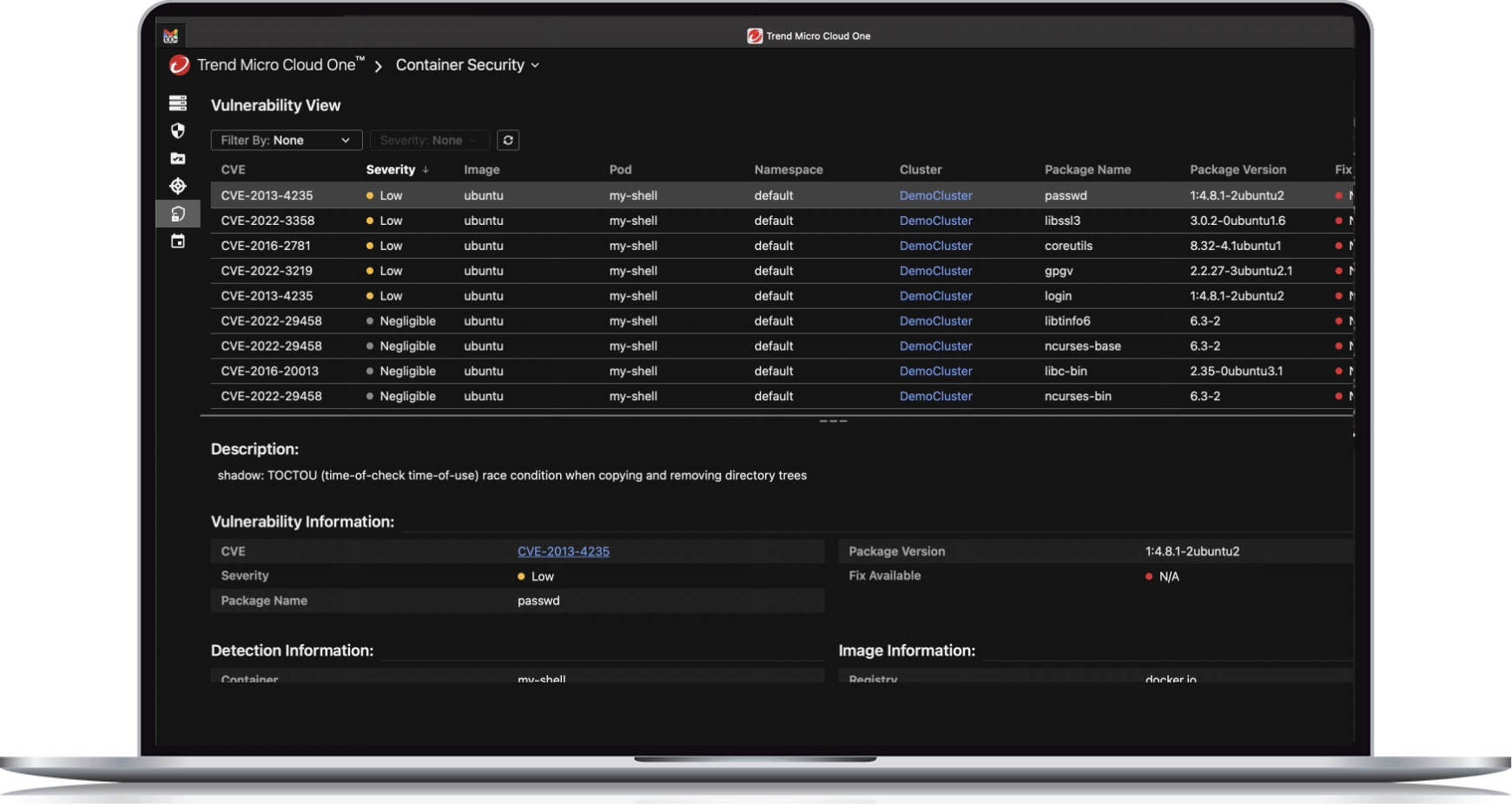
Identify fixes anywhere in your pipeline
- Uncover vulnerabilities, malware, and sensitive data, such as API keys and passwords, within your container images
- Detailed scans with recommended fixes anywhere in your pipeline
- Address vulnerabilities before they can be exploited at runtime
- Minimize false positives by correlating patch layers with packages that are vulnerable in the same image
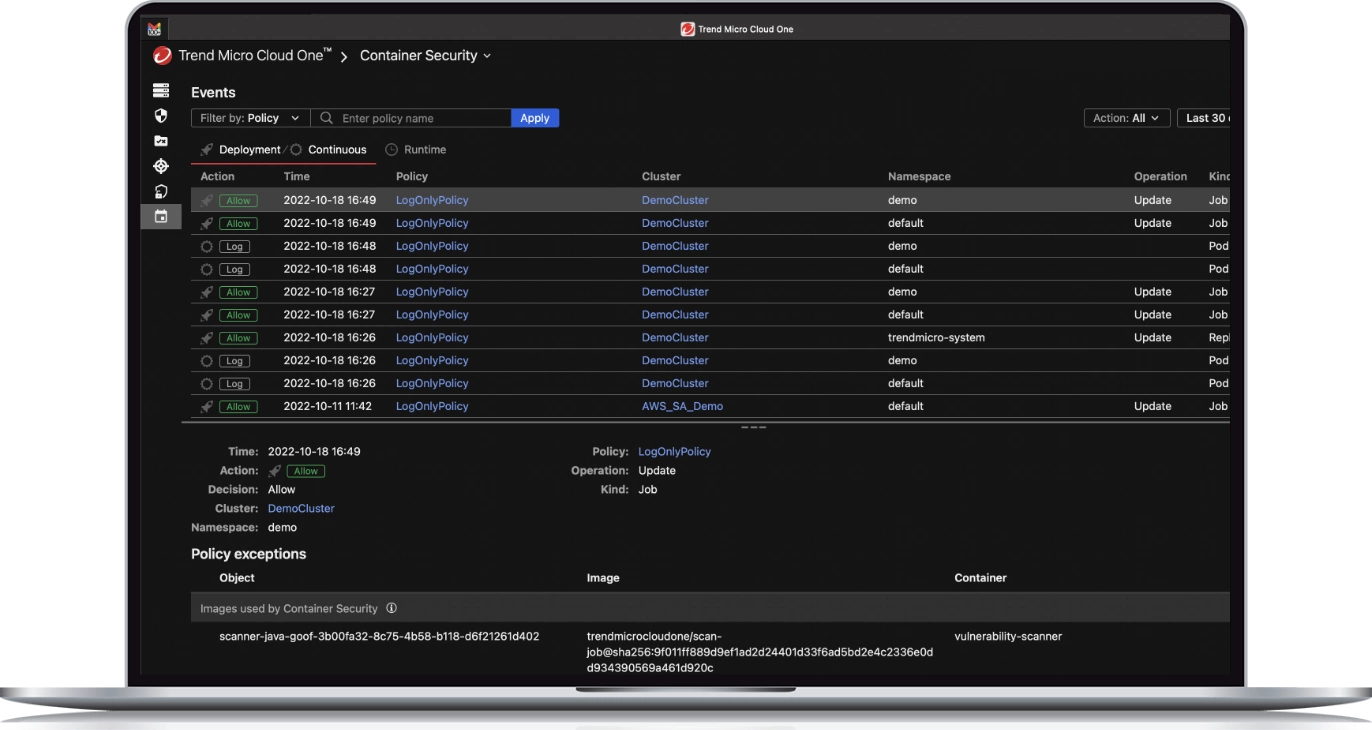
Enable developers to develop at ease
- Enable developers to remediate security issues before deployment via their existing tools and workflows
- Share common policies across multiple pipelines and remove the need to hard-code rules to deal with scan results
- Easily review scan results through command lines or tool suite scripting language –no security expertise required
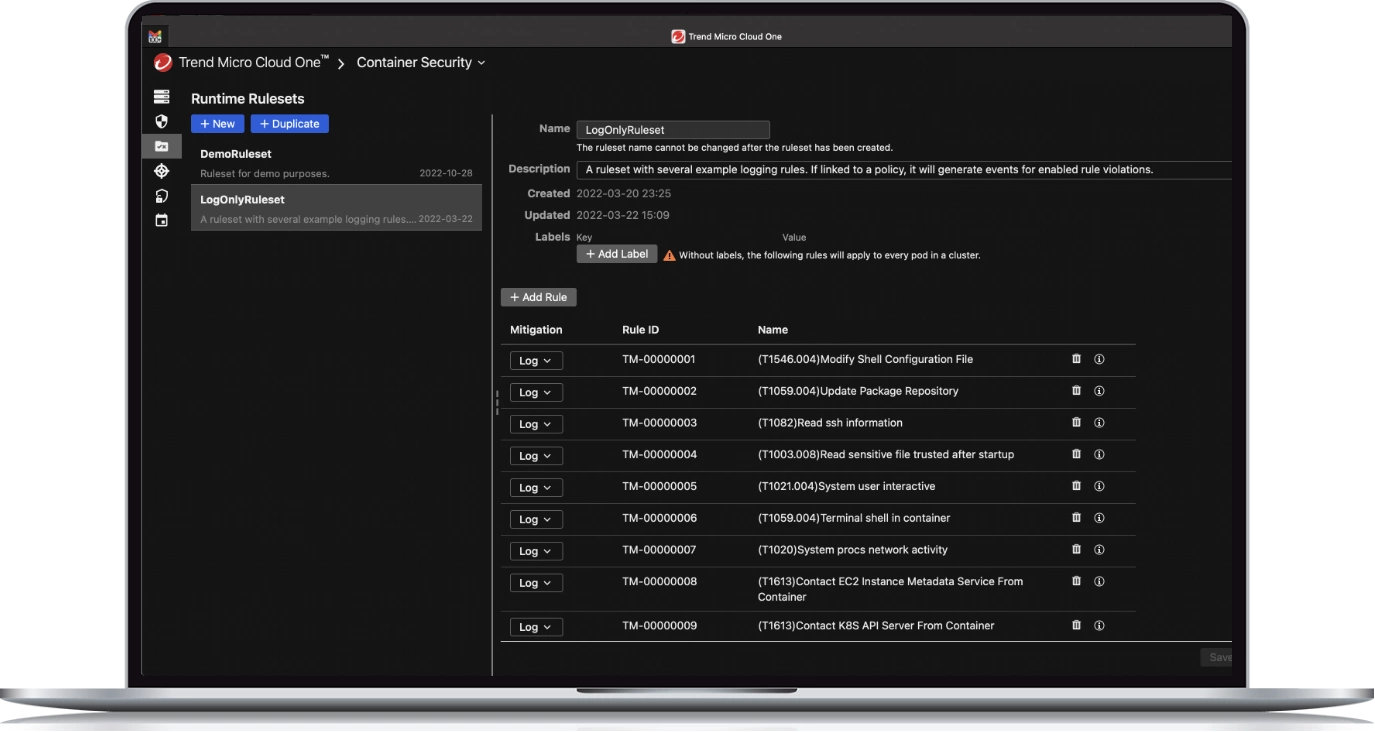
Ensure the security of your containers
- Detect security issues early, enforce admission policies, and be assured only secure and compliant containers run in production
- Allow images that only meet specific application or organization security policies to proceed through the pipeline
- Select from advanced policies, such as disallowing privileged containers or allowing exceptions based on names or tags
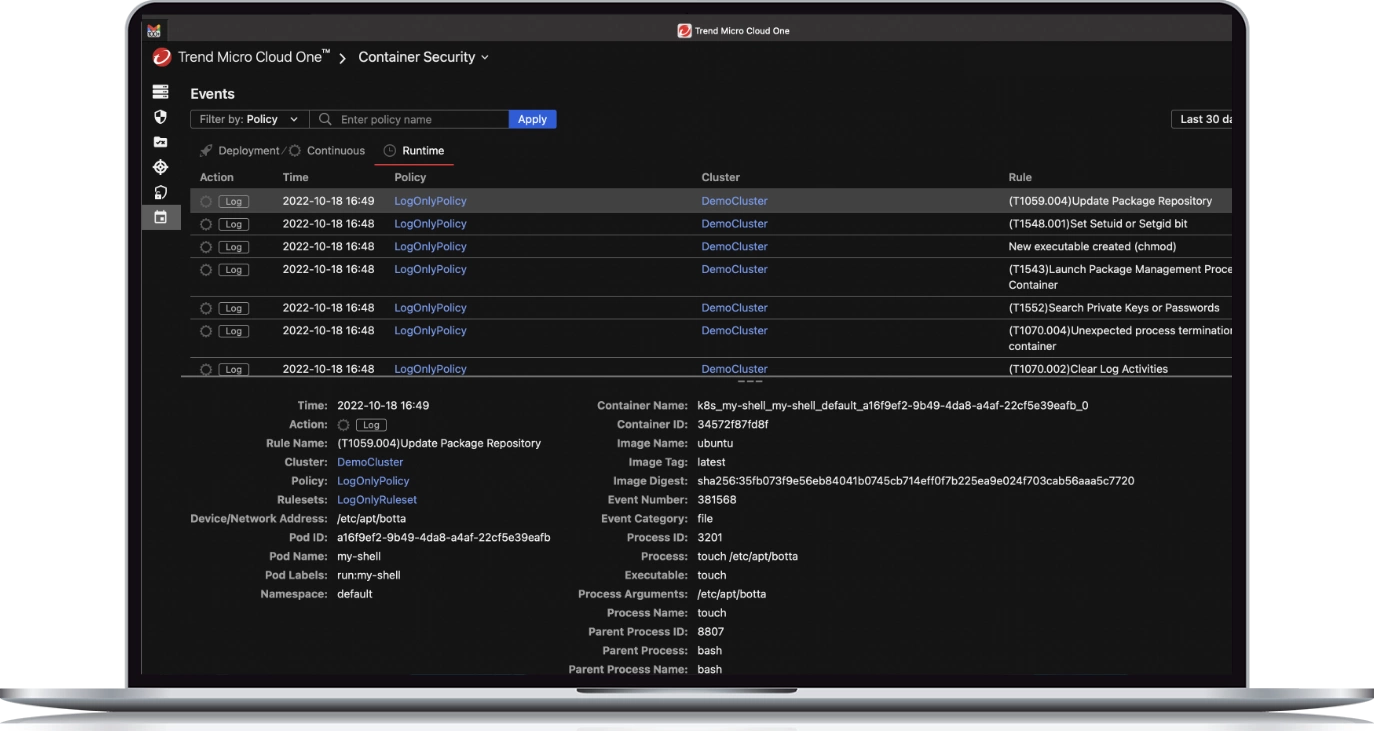
Full visibility, fast protection
- Get instant visibility of vulnerable running containers and serverless containers with insights aligned with the MITRE ATT&CK framework
- Discover attempts to run disallowed commands or illegally access files
- Runtime protection exposes container drift and builds a model of expected behavior via Learning Mode
Market-leading performance


Representative Vendor March 2023 Gartner® Market Guide for Cloud-Native Application Protection Platforms


Ranked #1 in IDC’s Worldwide Cloud Workload Security Market Shares report


#1 performer in Linux, detecting and preventing 100% of attacks against the Linux host


73% of organizations said they have significantly increased their efforts to secure container images
Trend Cloud One
Gain meaningful intelligence for security and developers with a powerful cloud-native application protection platform (CNAPP) that does more. Deploy security your way.

Forrester Total Economic Impact Study
Discover the projected cost savings and business benefits of Trend Cloud One, our security services platform, which includes File Storage Security and more.
Explore related resources
Other Trend Cloud One services
Container Security is part of Trend Cloud One, a security services platform for cloud builders, which includes:

Workload Security
Runtime protection for workloads (virtual, physical, cloud, and containers)

Network Security
Cloud network layer IPS security

Conformity
Cloud security and compliance posture management

File Storage Security
Security for cloud file and object storage services

Open Source Security by Snyk
Visibility and monitoring of open source vulnerabilities and license risks

Cloud Visibility
Inspect your environment in minutes, gain insight into threats, and remediate – all with one platform.
TRANSFORMING CYBERSECURITY
Get started with Container Security